Policy Monitor recently exhibited at the International Cyber Security Expo 2024 at London Olympia in the IASME Pavilion. It was a great opportunity to hear the real-life issues and challenges from attendees and to take questions from the press. Here are a few of the questions and the responses from the Policy Monitor team.
What are the latest emerging trends in cyber security?
Cyber security threats and solutions continue to evolve rapidly. At Policy Monitor, we aim to stay ahead of the curve. For example, criminals have created ‘Ransomware-as-a-Service’ offerings for other criminal gangs to exploit.
SME’s need access to protective technology to minimise the risk of a successful ransomware attack as well as ensuring that uncorrupted backups of data are available so data can be recovered following an attack. Policy Monitor is simplifying access for SMEs to backup and recovery facilities.
AI is undoubtedly a challenge and a game-changer and ChatGPT has democratised access to AI technology. Our horizon scanning research seeks to identify future risks. We intend to incorporate AI capabilities into our platform as we identify economic capabilities to protect organisations.
What makes Policy Monitor different?
What sets Policy Monitor apart is our focus on helping organisations of any size and for an affordable price to identify their weakest links, make appropriate investments to progressively strengthen protection, provide a consistent “all round defence” and optimise the benefits of those investments. Our customers can monitor their current situation across all aspects of their defensive posture, ensure the right balance between technology, monitoring, training and contingency planning.
Organisations can create an information security policy based on standard controls, selecting those that apply to them, verify their compliance against governance standards and frameworks.
Policy Monitor includes integrations with standard third-party technologies to simplify deployment and to consume data generated from those technologies to allow benefits to be realised with minimal effort. Products can be supplied through CSPM or by our partners who have brought their customers to CSPM.
Viewing a consolidated board portal through which organisations understand the threats, the specific risk associated with each threat, the extent to which staff are following policy to mitigate that risk, monitoring the attacks taking place and any near misses that have occurred, brings into sharp relief the value of protection and the places where more action is required.
Recognising that the human element still creates cyber security’s biggest vulnerabilities Policy Monitor continues to offer and expand comprehensive employee training.
How should organisations respond to evolving cyber threats?
The key advice is not to bury your head in the sand. Criminals just want to steal your money or things that they can sell for money. Putting in place a robust level of technical protection is simple for a competent system administrator and doesn’t need to be excessively expensive. The government provides many resources to help. First read the Cyber Essentials and IASME cyber security question sets and do what you can, even if you don’t choose to seek certification against those standards immediately—every action takes you forward to a better place.
It is important to carry out a risk assessment. Using a reputable consultant to help can be very beneficial, because they will have checklists and templates. However, your team understands your business best. It should be possible for your team to do most of the work.
Where should people start?
Investigate what cyberattacks are taking place—how they are perpetrated and get people asking the question could this happen to us?
Investigate if you have been hacked, by searching the dark web and scanning your systems.
Define your business processes, assess the weaknesses in them, the risks you face and the highest priority measures to take, for example the process of maintaining customer details, issuing a PO, authorising an invoice and paying the right account. Maintain a log of successful attacks or near misses and ensure these are highlighted when onboarding new employees.
Get system administrators to review the IASME question sets, report on the likelihood of immediately passing such audits, explain what threat each technical control is seeking to address and create an estimate of costs to implement each control.
Finally, understand your legal obligations and the impact on stakeholders if you fail to meet them. This level of analysis should result in an information security policy.
Implementing your protection?
So now it is time to put that policy into action. Do it in stages, create momentum, ensure that you monitor progress and identify policies breaches and take corrective action. Otherwise, your investment in technology, training and process is wasted!
Maintain training and awareness related to attacks and near misses and ensure people understand the seriousness of this to the survival of the business and to individuals’ reputations. Regularly practice incident management to test your recovery processes.
Identify weak points and review risks, therefore justifying further improvements to policy and investment in protective measures.
Verify that you can meet your obligations following an attack, for example have advisors appointed where appropriate, they have verified your plans and as a consequence you will be able to provide them with the information required.
Cyber security is an ongoing process not a one-off exercise, because criminals are constantly identifying new ways to attack and so you need to keep monitoring the situation to prove the continued effectiveness of your solutions, processes and technology.
There is a long history of organisations being breached via attacks to organisations in their supply chain, therefore it is vital the board regularly reviews the information security policy, the risk register and the performance of employees, contractors and supply chain partners.
Our approach at Policy Monitor is to make it simple to get going, to help you understand the risks, to build a business case to justify your investment, for you to progressively improve your maturity, your understanding of the risks, the effectiveness of your defences while minimising the burden of your organisation. You can then best understand how to respond to those risks with the resources you have available.
What is causing an increasing awareness of cyber threats?
The steady stream of cyber attacks faced by all types of organisations which hit the headlines in 2024 has meant that cyber security has jumped up the priority list for businesses of all sizes. Different types of incidents including data breaches, ransomware attacks and the unavailability of key systems have occurred for example at the NHS, Transport for London, BBC, British Library, MOD and several police forces.
The increased cyber threats emanating from Russia, China and North Korea have also been spotlighted in the news due to current conflicts and tensions around the globe, further increasing awareness.
To top things off, in July a faulty update to CrowdStrike’s Falcon sensor software caused a widespread outage that affected Microsoft Windows users worldwide. While this wasn’t due to a cyberattack the resulting chaos disrupted many individuals, industries and governments, including airlines, airports, banks, hospitals, and stock markets. This illustrated how much we all rely on IT and how interconnected and fragile our digital world can be.
What is the best way to turn awareness into action?
It is vital that a positive “what’s in it for me” is maintained. There must be a feedback loop to explain the changing risk profile to galvanise all stakeholders to action. Updates on changing external risks and risks related to any failure to follow policy that expose the organisation must drive oversight and action.
A clear focus on UX, user design and user experience, is vital for solutions. The user experience has to be excellent to: be intuitive, easy to understand, implement and keep updated. To make a complex topic simple to embed into an organisation and to deliver ongoing value. Turn policy into processes so every organisation can demonstrate good governance of its information security policy.
Ever changing regulations relating to cyber security and supply chain resilience in the UK, EU and beyond, such as NIS2 and DORA, will require organisations to meet internationalised standards of security. Compliance frameworks will cover multiple geographical regions in multiple languages. This will be a prerequisite for doing business in certain countries and industries.
On occasions expert third party advice may be needed to marshal a collaborative set of technology and consultancy suppliers to support businesses with a standard approach to a common enemy while embracing regulation across multiple jurisdictions within an international economic model.
How can Policy Monitor help?
Policy Monitor’s cloud-based solution Cyber Security Policy Monitor (CSPM) guides organisations to stay safe and achieve compliance. It is designed to help organisations to do the simple things first with the minimum of external support, to provide feedback on technical threats and justify the effort of stakeholders to embrace an organisation’s information security policy.
A staged approach, for example by certifying against Cyber Essentials, then IASME Assurance and lastly ISO 27001 gives a staged approach based on material progress and associate milestones.
CSPM supports English UK, English US, French, Spanish and Arabic to become an international solution.
End user organisations can invite consultancy organisations on the platform into their profile and hence facilitate controlled access to their data so that consultant can provide instant assistance when required.
We integrate with technologies for vulnerability assessment, backup and recovery, mobile device monitoring to extract information from those sources to inject evidence into tasks to prove the situation and demonstrate compliance. We can add to these technologies by customer request.
CSPM ensures you know what to do and when to do it to maintain a secure state. It provides reports and alerts senior management on the level of compliance within their company’s security policies. CSPM provides an evidence trail that can be referenced in the event of a breach or resulting litigation.
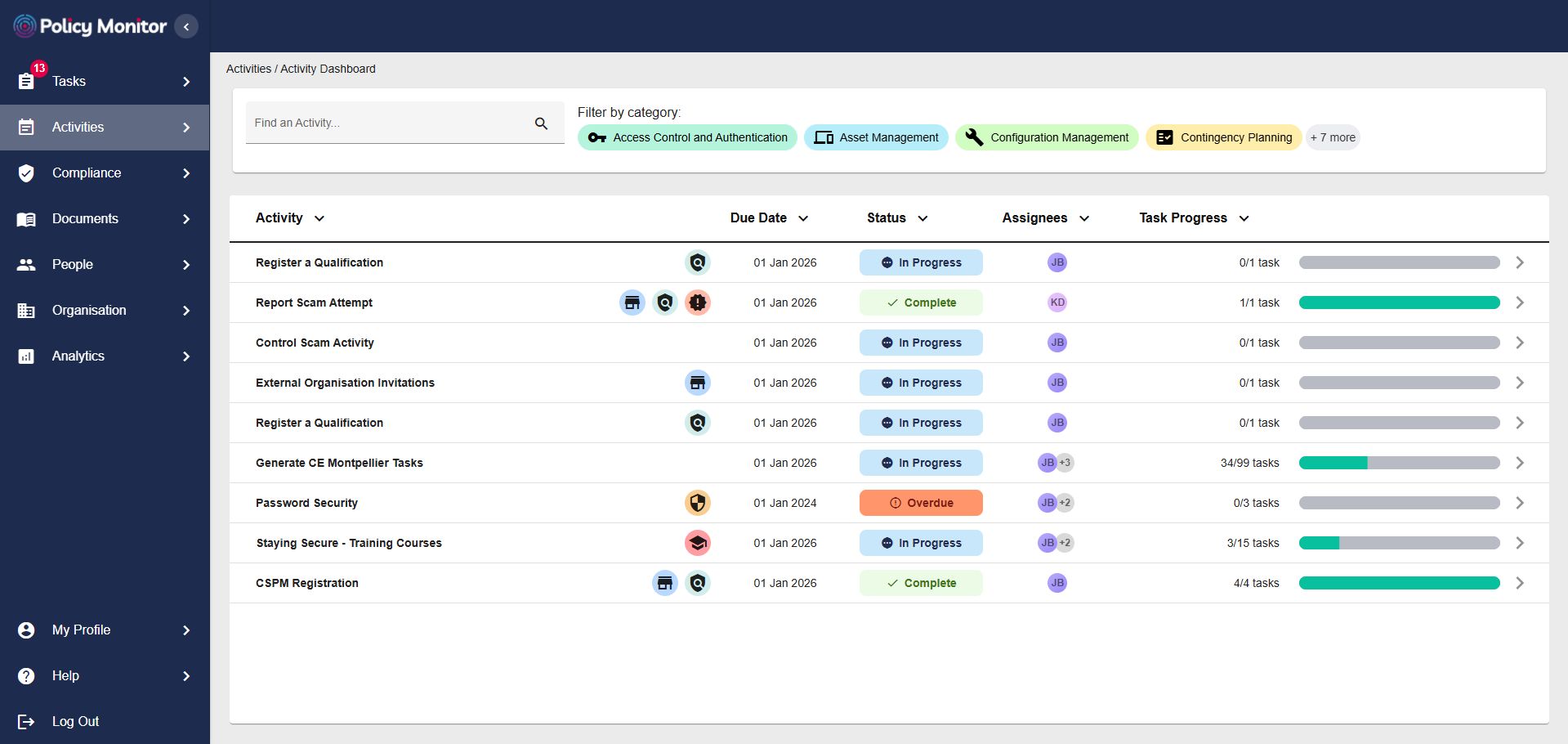
Administrators maintain oversight on their organisation’s ongoing workflows with the Activities Dashboard. See which users are working on what tasks, their progress on those tasks, and send out reminders to prompt users with outstanding actions left to complete.
By using CSPM, organisations can implement their information security policy, monitor the status of their hardware, improve their online security postures and protect against the vast majority of common cyberattacks, all at a very modest price that is no barrier to adoption.
